Deployment Readiness Checklist
How to use this guideThe deployment readiness checklist will help you prepare your environment and gather the necessary pieces of information to make deploying CLICK easy and painless.
The steps in this document are arranged in a logical order for performing them. The checklist template document is arranged in the order you will need the data points while deploying CLICK. To help connect the two, each data point is numbered, and this guide will reference data points using those numbers.
Download the checklist document and fill in the values as you proceed through your configuration to ensure you are completely prepared at deployment time.
Deploying CLICK Requires preparation in three main areas, your AWS account, your Active Directory environment, and your SAML IdP.
AWS Account
To deploy and configure CLICK, you will need to deploy the CLICK AD Gateway component into your AWS account. The AD Gateway uses AWS Lambda and requires network access to your Active Directory Domain Controller via LDAP or Secure LDAP. You will need to configure two items prior to deploying the AD Gateway to enable this connectivity.
Subnets
Since the AD Gateway Lambda function must communicate with your Active Directory Domain Controller, it must be launched in a subnet inside one of your VPCs. Identify one or more subnets (we recommend at least two) that meet the following requirements and make note of their IDs in Item 3.1.17 in the checklist document. CLICK Deployment
The subnets must
- Have a route to your Active Directory Domain Controller,
- Have a route to the Internet, and
- Allow outbound Internet traffic on port 443.
Security Group
The AD Gateway Lambda function's network permissions will be determined by a security group you assign to it. Select or create a security group that meets the following conditions and make a note of its ID in Item 3.1.16 the checklist document.
The security group must
- Allow outbound requests on your LDAP port (normally 389 or 636) and
- Allow outbound requests on port 443.
User / Role ARN
When deploying the AD Gateway CloudFormation template, you will need to specify a user or role ARN. The CloudFormation template creates a KMS key, and this ARN will be used to control the policies governing access and use of the key.
Identify the user or role that will be in use when deploying the CLICK AD Gateway CloudFormation template. Record this ARN in both Item 3.1.9 and Item 3.1.10 in the checklist document.
We use the same value in two places becauseYou can later create an update set for the CloudFormation stack and remove the value for
ClickKMSKeyEncrypterArn, ensuring the AD Gateway Lambda function is the only entity allowed to decrypt and read your secure AWS Systems Manager parameters.
Active Directory
The Amazon WorkSpaces service is dependent on Active Directory because WorkSpaces are tied to individual Active Directory users. CLICK uses Active Directory in part to ensure that it can reference those same users when creating WorkSpaces. But, CLICK also uses your Active Directory group and OU structures (with some configuration from you) to make decisions about which users should have WorkSpaces and what configurations those WorkSpaces should have.
There are a number of steps and data points for this part of the configuration. But, don't be intimidated! Many of these are optional, and only exist to allow you to fine-tune the way CLICK interfaces with your Active Directory environment. This is sensitive data, and many organizations have strict policies to adhere to. We want to provide you with all the tools you need to succeed while remaining in compliance.
Domain Controller
Identify one or more domain controllers for the CLICK AD Gateway to communicate with. Record their FQDNs in Item 3.1.4 in the checklist document.
LDAP Details
Record the port you will use for LDAP communication in Item 3.1.7 in the checklist document. The default port for LDAP is 389, and the default port for Secure LDAP is 636.
If you are using Secure LDAP, make sure to change the value to true in Item 3.1.20 in the checklist document. You will also need access to the private key of your LDAP certificate. There is a space for this in Item 3.2.2 in the checklist document, but we recommend you do not write down the private key in plaintext. Let the item in the checklist document serve as a placeholder, and store the private key securely for when it is needed.
Service User
The AD Gateway Lambda function needs to authenticate its LDAP calls to your Active Directory Domain Controller. Create or select a service account to use for this purpose, and capture the User Principal Name in Item 3.1.8 in the checklist document.
You will also need the password, and there is a space for it in Item 3.2.1 in the checklist document, but we recommend you do not write down the password in plaintext. Let the item in the checklist document serve as a placeholder, and store the password securely for when it is needed.
We recommend an account that
- Is not used for any other purpose,
- Has read-only access to Active Directory data, and
- Has a strong, non-expiring password.
Authorization Security Groups
CLICK uses group membership for authorization, determining what a user is allowed to do. Part of the process of setting up a CLICK instance is identifying the groups that will control CLICK's three major permission sets:
- Administrators - Have rights to perform all setup and configuration within CLICK and take actions on WorkSpaces.
- Self-Service Users - Have the ability to start, stop, and reboot WorkSpaces that are assigned to them.
- Self-Service Rebuild Users - Have the ability to rebuild WorkSpaces that are assigned to them.
Create or select an Active Directory group for each of these roles.
We recommendAdding at least one user to these groups so you can log into CLICK immediately after completing your deployment to verify that everything is working as expected.
Find the objectGUID attribute of each group and record the GUIDs in Items 1.1, 1.2, and 1.3, respectively. You can find the objectGUID of a group by opening the group's properties in the Active Directory Users and Computers management console and going to the Attribute Editor tab. The objectGUID will be one of the many attributes listed here.
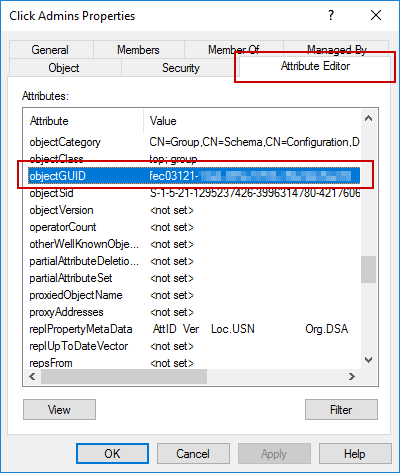
Unfortunately, the Attribute Editor doesn't provide a way to copy the GUID value. The simplest way to get the GUID in a way that you can copy it is to look it up using PowerShell. Find the Group's distinguishedName attribute in the Attribute Editor.
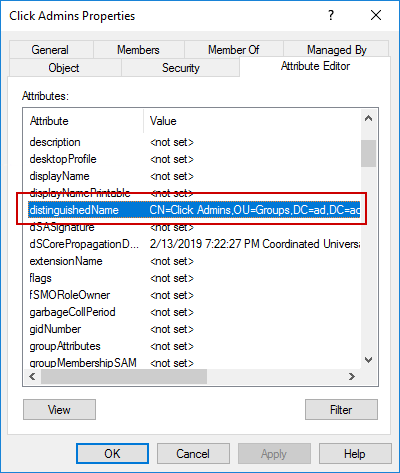
Double click on the entry to bring up the String Attribute Editor window, then copy the entire string.
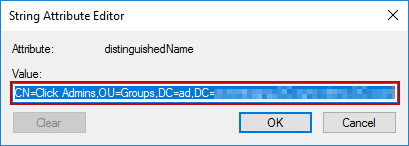
Finally, paste the distinguishedName value in place of __value__ in the below script and execute it.
Get-ADObject -Identity "__value__" | Select-Object -Property ObjectGUIDOrganizational Units
The CLICK AD Gateway only queries the OUs you specify for users and groups. Create or select the OUs you plan to use for storing CLICK-related users and groups. CLICK will only have visibility to the OUs you specify.
We recommend
- Isolating CLICK-related groups in their own OUs to avoid clutter inside of CLICK.
When you have identified all OUs you wish to use for CLICK groups, record their distinguished names in Item 3.1.2 in the checklist document.
When you have identified all OUs you wish to use for CLICK users, record their distinguished names in Item 3.1.5 in the checklist document.
Advanced Options
Have a look at the AD Gateway Stack Parameters documentation for some of the more advanced options you can configure when deploying the CLICK AD Gateway.
SAML IdP
The last thing you will need to prepare is your SAML Identity Provider (IdP). We have step-by-step guides for some of the most common providers, but CLICK will work with any SAML 2.0 compliant provider.
Follow the guide for your specific SAML provider below.
Once you have completed configuring your SAML integration, make note of the metadata document URL in Item 2.1 in the checklist document. Lastly, put the UPN suffix your users will use when logging into CLICK into Item 2.2 in the checklist document.
If a user would log into CLICK using[email protected], the UPN suffix you should provide issynchronet.com.
Checklist Verification
At this point, you should have performed all the necessary configuration to enable a straightforward deployment of CLICK into your environment. Before continuing, take a moment to review your completed checklist document.
At a minimum, you should have values for the following items (some of these may be defaults, and that is fine):
Item No. | Name | Sample Value |
|---|---|---|
1.1 | Admin Group GUID |
|
1.2 | Self-Service Group GUID |
|
1.3 | Self-Service Rebuild Group GUID |
|
2.1 | Metadata Document URL |
|
2.2 | Identifiers |
|
3.1.2 | AdGroupsOUs |
|
3.1.4 | AdHost |
|
3.1.5 | AdPeopleOUs |
|
3.1.7 | AdPort |
|
3.1.8 | AdUser | |
3.1.9 | ClickKMSKeyAdminArn |
|
3.1.10 | ClickKMSKeyEncrypterArn |
|
3.1.11 | CodeDeployBucket |
|
3.1.14 | SSMPrefix |
|
3.1.15 | ScheduleRate |
|
3.1.16 | SecurityGroupIds |
|
3.1.17 | SubnetIds |
|
3.1.20 | UseSecureLdap |
|
3.2.1 | /click/ad/password | should be securely stored elsewhere |
As long as you've got all of these values, congratulations, you are ready to deploy CLICK!
Updated 9 months ago
